Holistic Company Security: Corporate Security Techniques Revealed
Wiki Article
Tailored Corporate Safety And Security Solutions for Your Distinct Service Needs
In today's increasingly complicated business landscape, guaranteeing the safety and security and protection of your organization is of critical relevance. At [Business Name], we acknowledge that every service has its own distinct collection of safety demands. That is why we provide tailored company safety options designed to resolve the specific challenges and susceptabilities of your company. Our group of experienced specialists will work carefully with you to examine your particular safety demands and create extensive techniques to minimize dangers and safeguard your assets. From tailoring monitoring systems to implementing accessibility control procedures and improving cybersecurity, our remedies are created to provide ideal defense for your sensitive data and vital operations. With our continuous support and upkeep, you can relax guaranteed that your unique safety and security needs are continually satisfied. Trust [Firm Name] to deliver the tailored safety and security solutions your service is worthy of.Examining Your Certain Protection Requirements
To efficiently address your company's security concerns, it is vital to conduct a comprehensive evaluation of your details safety demands. Understanding the unique risks and susceptabilities that your organization deals with is necessary for establishing an effective security strategy. Without a correct analysis, you might assign resources inefficiently or overlook essential locations of susceptability.
The primary step in examining your details safety and security requirements is to conduct a complete examination of your physical facilities, including structures, parking lot, and access factors. This assessment needs to recognize prospective weak points such as insufficient lights, out-of-date security systems, or prone access points. In addition, it is essential to analyze your organization's electronic security by evaluating your network facilities, information storage, and security methods. This will assist identify prospective susceptabilities in your IT systems and identify the needed measures to secure sensitive details.
One more crucial aspect of examining your safety and security requires is comprehending your company's one-of-a-kind operational demands and compliance commitments. This consists of considering aspects such as the nature of your industry, the value of your possessions, and any type of regulative or legal needs that may use. By understanding these details factors, you can tailor your security measures to fulfill the details demands of your service.
Personalizing Monitoring Solutions for Ideal Protection
Customize your surveillance systems to supply optimum defense for your business. When it concerns guarding your company and its assets, a one-size-fits-all technique merely will not be enough. Every company has its own special safety and security demands, and personalizing your surveillance systems is vital to guaranteeing that you have one of the most reliable protection in position.Firstly, it is very important to perform a comprehensive assessment of your properties to determine susceptible areas and possible safety dangers. This will aid establish the kind and number of cameras required, in addition to their tactical placement. Risky areas such as entries, car park, and storage facilities might need advanced security innovation, such as high-resolution electronic cameras or night vision abilities.
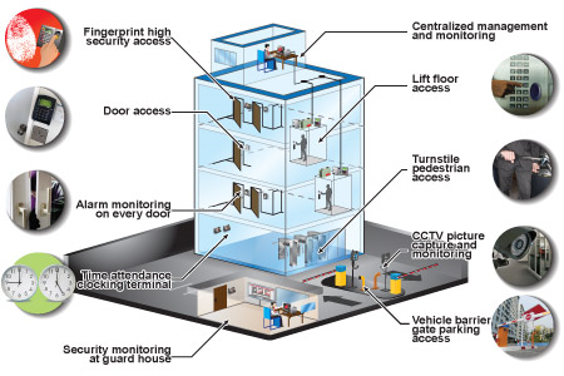
Incorporating your surveillance systems with other safety actions, such as accessibility control systems or alarm systems, can additionally enhance the efficiency of your total safety approach. By personalizing your security systems to straighten with your learn the facts here now particular organization requirements, you can have satisfaction knowing that your properties, employees, and consumers are safeguarded to the fullest degree possible.
Implementing Tailored Gain Access To Control Actions
For ideal protection, business need to apply tailored accessibility control steps that line up with their unique business needs. Access control measures are vital in securing sensitive details and making sure that only authorized individuals have accessibility to certain locations or sources within a company. By customizing access control actions, business can establish a durable safety system that efficiently reduces safeguards and dangers their assets.Applying tailored access control actions includes several crucial steps. A detailed analysis of the business's protection needs and prospective susceptabilities is required. This analysis ought to take into consideration elements such as the nature of the business, the value of the details or possessions being safeguarded, and any type of regulatory or compliance needs. Based on this evaluation, companies can then determine the proper gain access to control devices to apply.
Access control actions can consist of a combination of physical controls, such as badges or keycards, as well as technological solutions like biometric authentication or multi-factor authentication. These procedures can be implemented across numerous access factors, such as doors, gates, or computer system systems, depending upon the business's certain requirements.
In addition, business have to develop clear plans and treatments relating to gain access to control. This includes defining responsibilities and roles, setting up user accessibility degrees, frequently evaluating gain access to opportunities, and checking accessibility logs for any kind of dubious tasks. Regular training and recognition programs need to also be conducted to guarantee workers know the significance of gain access to control and abide by established procedures.
Enhancing Cybersecurity to Guard Sensitive Information
Executing durable cybersecurity steps is important to successfully safeguard sensitive information within a business. In today's digital landscape, where cyber risks are becoming progressively innovative, businesses must focus on the defense of their beneficial info. Cybersecurity includes a variety of techniques and technologies that intend to avoid unauthorized gain access to, data violations, and other harmful activities.To enhance cybersecurity and guard sensitive information, business must execute a multi-layered technique. In addition, executing strong gain access to controls, such as multi-factor verification, can aid stop unapproved accessibility to delicate systems and information.

Furthermore, companies need to have a case feedback strategy in location to efficiently respond to and reduce any type of cybersecurity cases. This plan ought to detail the actions to be absorbed the event of a data violation or cyber strike, including communication protocols, control procedures, and recuperation approaches.
Recurring Support and Upkeep for Your Unique Demands
To guarantee the ongoing performance of cybersecurity actions, continuous support and maintenance are crucial for resolving the advancing threats encountered by companies in safeguarding their delicate information. In today's rapidly transforming digital landscape, cybercriminals are frequently discovering brand-new methods to exploit susceptabilities and breach safety systems. For that reason, it is critical navigate to this site for organizations to have a durable support and upkeep system in position to remain ahead of these dangers and protect their useful details - corporate security.Recurring assistance and maintenance involve consistently upgrading and covering safety and security software application, monitoring network activities, and conducting vulnerability evaluations to recognize any kind of weaknesses in the system. It also includes offering prompt help and advice to employees in executing safety ideal techniques and reacting to possible security incidents.
By buying recurring assistance and upkeep solutions, services can take advantage of positive tracking and detection of prospective risks, as well as prompt response and remediation in the event of a security breach. This not only helps in reducing the effect of an assault yet also makes certain that the company's security posture remains versatile and strong to the evolving risk landscape.
Verdict

To effectively address your company's security issues, it is vital to conduct read the article a detailed analysis of your specific safety demands. Every business has its own one-of-a-kind security requirements, and personalizing your surveillance systems is essential to making certain that you have the most effective security in area.
For optimal security, business need to carry out tailored gain access to control actions that line up with their one-of-a-kind company demands.In conclusion, tailored corporate security services are necessary for companies to address their one-of-a-kind safety demands. By analyzing certain safety demands, personalizing monitoring systems, carrying out tailored access control actions, and boosting cybersecurity, services can secure and secure sensitive data versus possible dangers.
Report this wiki page